Critical Stagefright flaw, millions affected
In late July, researchers with Zimperium announced the discovery of a critical flaw in the Android library libstagefright, potentially affecting 95% of all Android devices, from Android Froyo (2.2) to Lollipop (5.0). The flaw could result in the device getting owned if successfully exploited.
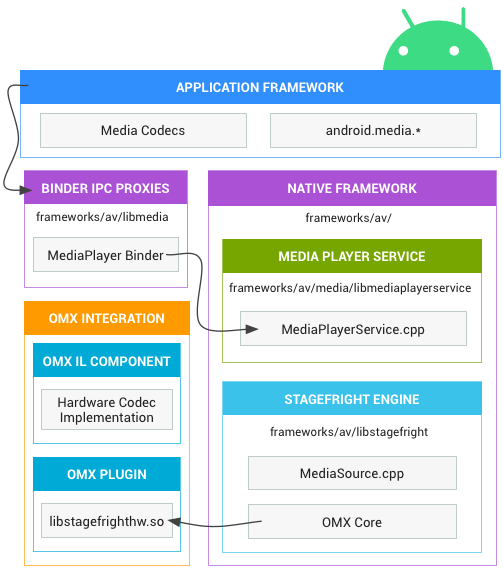
Google illustrates Android media architecture and framework in the following diagram:
Zimperium describes the vulnerability as the following:
“These issues in Stagefright code critically expose 95% of Android devices, an estimated 950 million devices. Drake’s research, to be presented at Black Hat USA on August 5 and DEF CON 23 on August 7 found multiple remote code execution vulnerabilities that can be exploited using various methods, the worst of which requires no user-interaction.
Attackers only need your mobile number, using which they can remotely execute code via a specially crafted media file delivered via MMS. A fully weaponized successful attack could even delete the message before you see it. You will only see the notification. These vulnerabilities are extremely dangerous because they do not require that the victim take any action to be exploited. Unlike spear-phishing, where the victim needs to open a PDF file or a link sent by the attacker, this vulnerability can be triggered while you sleep. Before you wake up, the attacker will remove any signs of the device being compromised and you will continue your day as usual – with a trojaned phone.”
Not to be sensational, but that sounds disturbing to say the least. There are seven vulnerabilities related to their research, each was assigned a Common Vulnerabilities & Exposures (CVE):
- CVE-2015-1538
- CVE-2015-1539
- CVE-2015-3824
- CVE-2015-3826
- CVE-2015-3827
- CVE-2015-3828
- CVE-2015-3829
In light of the disclosure, Google has updated its code to include a fix for the vulnerabilities. Historically, Android code fixes take months to be distributed to device manufacturers. At the time of this writing, only two manufacturers have updates available, Google Nexus and Samsung Note 4.
Mitigation
In the meantime, there are steps you can take to minimize your risk of receiving and activating malformed media files that attempt to harness the Stagefright vulnerabilities to execute arbitrary code:
1. Update your device regularly – when a software update is made available it will be installed
2. Disable Auto-downloading of MMS, include Hangout and regular messaging apps
HANGOUT: Disable Auto Retrieve MMS
Open Hangout
Tap Options on the top left corner
Tap Settings -> SMS
In the Advanced uncheck Auto Retrieve MMSMESSAGES: Disable Auto Retrieve MMS
Open Messages
Tap More -> Settings -> More Settings
Tap Multimedia Messages -> Turn OFF Auto Retrieve.
Avast Labs created some additional instructions to assist customers in helping to mitigate this collection of vulnerabilities, here.
Detection added
0xID Labs reviewed vulnerabilities and added coverage to our cloud detection engine, particularly for two of the CVEs, -1538 and -3824. We will continue to monitor this vulnerability disclosure as more details are divulged. We urge our customers to use their devices cautiously while the Stagefright vulnerabilities are being announced at Black Hat as hackers are likely to tighten and/or expand exploitation of these vulns.
0xID Labs
- IoT
- Android
- Black Hat
- Hacking
- privacy
